As you may be aware, Oracle have released the next installment of their PaaS Integration products: Oracle Integration Cloud. Don't be alarmed, the Oracle Integration Cloud is not a brand new product, but it is rather a bundle of existing PaaS offerings.
A new option has been added under the PaaS Integration options: 'App Integration' (Oracle Integration Cloud).
Oracle Integration Cloud comes with:
- Integrations (ICS)
- Processes (PCS)
- Visual Builder (VBCS, previously known as ABCS)
- Insights / Integration Analytics
Oracle Integration Cloud, Oracle's compelling new cloud offering combines Application Integration, Process Automation, Visual Application Building and Integration Analytics into one unified cloud service.
It can be confusing when comparing to the previous singular offerings, but here is a good summary of OIC/ICS/SOACS by Phil Wilkins: Blogpost
Oracle Cloud Integration instance
Now let's crack on with creating an Oracle Integration Cloud instance:
There are pre-requisites before setting up Oracle Integration Cloud. You must have the following Oracle Cloud Services already setup:
1. Oracle Storage Container (See blogpost here)
2. Oracle Cloud Database (See blogpost here)
1. Once logged into Oracle Cloud, from the Dashboard menu, click on the 'Integration Cloud' option:
2. On the Oracle Integration Cloud Service page, click 'Create Service':
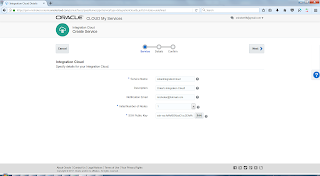
3. Integration Cloud - Specify details for your Integration Cloud:
4. Integration Cloud Details - Specific details for your Integration Cloud:
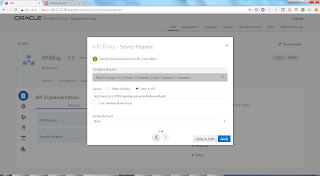
Note: Feature Set by default is 'Integration and Process', this means your OIC instance will consist of both Integration and Process (and the supporting tools). You can decide to select only Integration, this will mean your instance will not include Process. Think of an On-prem set up of the SOA Suite, you could have only the SOA Suite, but you can also have the SOA Suite with BPM.
Note 2: Cloud instances of Storage Container and an Oracle Database were pre-requisites, and the details will be entered here.
6. After clicking create, you will be redirected to the Integration Cloud Services page where you will see your new Integration Cloud instance with a Status of 'Creating Service':
7. Provisioning of your Integration Cloud instance takes just under an hour. Quite a lot going on behind the scenes. I cooked and ate my dinner during the provisioning, and just as I had finished, I received an email from Oracle notifying that my Integration Cloud instance was ready to use. :)
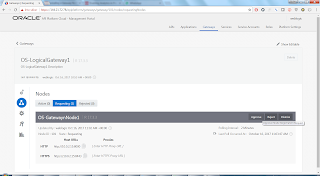
8. Click on your Integration Cloud instance to view an overview of the topology. Click on the services icon to view links to the instance Enterprise Manager, Admin Console or the Integration Cloud Home Page:
9. Click on 'Open Integration Cloud Home Page' and you will be taken to where all the magic will happen!
In further blogposts, I will cover some examples of Integrations, Processes and Visual Builder (Zero code apps). Stay tuned!